
Introduction
In recent news, Apple, the tech giant behind the iconic iPhone, has issued a cautionary alert regarding sophisticated spyware assaults reminiscent of the infamous Pegasus. These assaults are specifically targeted towards a narrow demographic, often including journalists, activists, politicians, and diplomats. Let’s delve deeper into the implications of such attacks and how individuals and organizations can protect themselves.
The Scope of the Threat
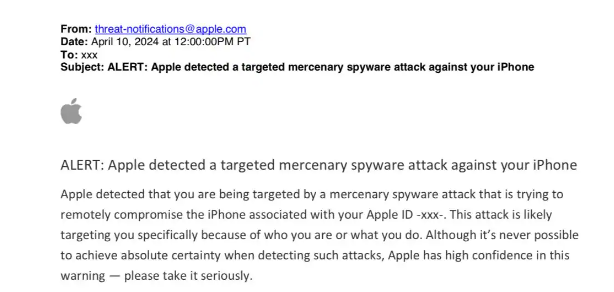
Apple’s security advisory, released on April 10, highlights the persistent and widespread nature of these targeted spyware assaults. Despite their limited focus and significant costs, these attacks pose a serious threat to individuals and entities worldwide. Historically, such assaults have been linked to governmental entities, as evidenced by various studies and reports.
Understanding Specialized Spyware
Specialized spyware differs from typical cybercriminal activities and ordinary malware in its precision and resources. Attackers allocate significant resources to target specific individuals and their devices. These assaults are highly sophisticated, with multimillion-dollar expenses and brief durations, making them challenging to detect and counteract.
The Pegasus Connection
The Pegasus spyware, developed by the NSO Group, is a notable example of specialized spyware. This spyware gained control over mobile devices simply by receiving a missed call on WhatsApp. Despite its targeting of a select few, Pegasus and similar tools are pervasive threats.
Also Read : Make Money Online with Openai Sora 2024 – Complete Tutorial
Safeguarding Against Specialized Spyware
Given the complexity and global reach of specialized spyware assaults, it’s crucial for users to take proactive measures to protect their devices and data. Apple recommends activating lockdown mode as one way to enhance device security. Additionally, staying informed about potential threats and employing security best practices can help mitigate the risk of falling victim to such attacks.
The Role of Organizations
Organizations also play a vital role in combating specialized spyware assaults, particularly as remote work becomes increasingly common. According to a survey by cybersecurity company Check Point, nearly half of organizations globally struggle to detect intrusions or breaches on employee-owned devices. With the mobile landscape emerging as a new frontier for corporate cybersecurity battles, organizations must prioritize mobile security measures.
Conclusion
Specialized spyware assaults represent a significant threat to individuals, organizations, and even governments. As demonstrated by Apple’s recent security advisory, these attacks are not to be underestimated. By remaining vigilant, implementing robust security measures, and staying informed about evolving threats, individuals and organizations can better protect themselves against the growing menace of specialized spyware.
Also Read : IPhone 16: The Tech Marvel You’ve Been Dreaming Of – Here’s the Inside Scoop on Apple’s Game-Changer!
FAQs
1. How can I tell if my device has been targeted by specialized spyware?
If you notice unusual behavior on your device, such as sudden battery drain, unexplained data usage, or strange pop-ups, it could be a sign of a specialized spyware assault. It’s essential to act quickly by running a security scan and seeking assistance from cybersecurity professionals if necessary.
2. Are there any specific industries or professions that are more vulnerable to specialized spyware assaults?
While journalists, activists, politicians, and diplomats are commonly targeted due to the sensitive nature of their work, anyone could potentially fall victim to specialized spyware assaults. Attackers may target individuals or organizations for various reasons, including financial gain, espionage, or sabotage.
3. What steps can I take to protect my device from specialized spyware?
To protect your device from specialized spyware, ensure that you keep your operating system and apps up to date, avoid clicking on suspicious links or attachments, use strong, unique passwords for all accounts, and consider installing reputable antivirus software or security apps.
4. Can specialized spyware assaults be traced back to their perpetrators?
Tracing specialized spyware assaults back to their perpetrators can be challenging due to the sophisticated techniques used by attackers to conceal their identities and origins. However, law enforcement agencies and cybersecurity experts continue to investigate such incidents to hold the responsible parties accountable.
5. What should I do if I suspect that my device has been targeted by specialized spyware?
If you suspect that your device has been targeted by specialized spyware, it’s essential to take immediate action to mitigate the damage. This may include disconnecting the device from the internet, performing a factory reset, and seeking assistance from cybersecurity professionals to thoroughly investigate and address the breach.